Protect your personal information and keep it private
Because it is possible for your name, address, phone number, and identity to be stolen, or made public, Microsoft Office, Windows, and Internet Explorer can help keep your personal information more private and secure. The following links take you to instructions that help you, your family, and your business protect one of your most important assets: your personal information.Preparing GDN for new TCRs and test cases
Online fraud and phishing
Protecting yourself against fraud starts with understanding fraud and the kinds of activities that expose you to the risk of fraud. To learn about how to identify likely fraud and practices that will help to protect you, see Protect yourself from phishing schemes and other forms of online fraud.
My privacy in Office
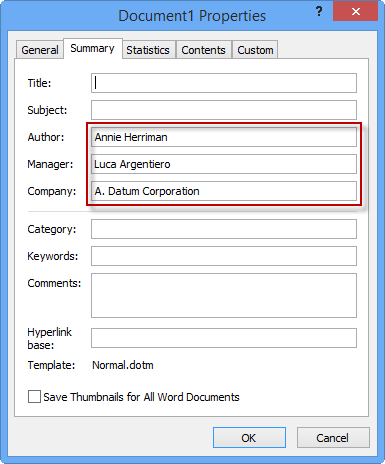
When using Office programs, it's important to know that personal information about you is stored in the file, such as Author (your name), Manager, Company, and Last Saved By. Additional information that can remain in the document is hidden text, revised text, field codes, or your email address. By using the instructions in the following articles, you can delete this information.
What version of Office am I using?
For instructions about how to discover the version of Office that you're using, see What version of Office am I using?
Office 2010, Office 2013, and Office 2016
The Trust Center in Office is where you can configure settings to help protect your privacy and the security of your computer and documents. For more information about the Trust Center, see View my options and settings in the Trust Center
You can make sure personal information doesn't get to the wrong person by removing it from your Office documents. For instructions in removing personal information, see the following topics:
Office 2007
You have the option of what information is shared with Microsoft, and this version introduced the Trust Center where you can make privacy and security choices that you want.
My privacy in Windows
You can use the following instructions for your operating system to make sure your privacy and personal information is protected. If you're not sure what version of Windows you have installed, click the following link.
What version of Windows do I have?
To automatically discover the version of Windows that your computer is running, see Which version of Windows do I have?
Windows 7: InPrivate browsing
InPrivate browsing prevents Internet Explorer from storing data about your browsing session. This helps to prevent anyone else who might use your computer from seeing the websites that you visited and what you looked at on the web. For more information about InPrivate browsing, see InPrivate browsing.
Windows Vista: Windows Defender
Windows Defender is a security tool for Windows Vista that helps detect and remove spyware from your computer. For more information about Windows Defender, see Using Windows Defender
My privacy in Internet Explorer
When you're shopping, browsing, playing games, or downloading pictures, you can make sure that your privacy is more secure when you're using Internet Explorer.
What version of Internet Explorer do I have?
You can automatically discover the version of Internet Explorer running on your computer by clicking the following link: Which version of Internet Explorer do I have?
Internet Explorer 8
Learn about cookie settings, Pop-up Blocker, and InPrivate browsing.
Internet Explorer 7
For Internet Explorer 7, you can help prevent being a victim of fraud and identity theft by adjusting your browser's privacy settings. For more information, see Change Internet Explorer Privacy Settings (versions 7 and 8)
thank you for your imformation,
ReplyDeletewincracker.com
iExplorer Crack
On first launch of vst crack, it will scan your system for known threats which may be hidden on your system and alerts you of anything suspicious.
ReplyDeleteI like your all post. You have done really good work. Thank you for the information you provide, it helped me a lot. crsoftz.com I hope to have many more entries or so from you.
ReplyDeleteVery interesting blog.
Advanced Identity Protector Crack
Is this a paid topic or do you change it yourself?
ReplyDeleteHowever, stopping by with great quality writing, it's hard to see any good blog today.
http://licensedinfo.com/
Advanced Identity Protector
NCH DreamPlan