Search the audit log in the Office 365 Security & Compliance Center
Need to find if a user viewed a specific document or purged an item from their mailbox? If so, you can use the Office 365 Security & Compliance Center to search the unified audit log to view user and administrator activity in your Office 365 organization. Why a unified audit log? Because you can search for the following types of user and admin activity in Office 365:
-
User activity in SharePoint Online and OneDrive for Business
-
User activity in Exchange Online (Exchange mailbox audit logging)
Important: Mailbox audit logging must be turned on for each user mailbox before user activity in Exchange Online will be logged. See Exchange mailbox activities.
-
Admin activity in SharePoint Online
-
Admin activity in Azure Active Directory (the directory service for Office 365)
-
Admin activity in Exchange Online (Exchange admin audit logging)
-
User and admin activity in Sway
-
User and admin activity in Power BI for Office 365
-
User and admin activity in Yammer
Here's the process for searching the audit log in Office 365.
Step 1: Run an audit log search
Step 2: View the search results
Before you begin
-
See the Audited activities in Office 365 section in this topic for a description of the user and admin activities that are logged in Office 365.
-
You (or another admin) must first turn on audit logging before you can start searching the Office 365 audit log. To turn it on, just click Start recording user and admin activity on the Audit log search page in the Security & Compliance Center. (If you don't see this link, auditing has already been turned on for your organization.) After you turn it on, a message is displayed that says the audit log is being prepared and that you can run a search in a couple of hours after the preparation is complete. You only have to do this once.
Note: We're in the process of turning on auditing by default. Until then, you can turn it on as previously described.
-
You have to be assigned the View-Only Audit Logs or Audit Logs role in Exchange Online to search the Office 365 audit log. By default, these roles are assigned to the Compliance Management and Organization Management role groups on the Permissions page in the Exchange admin center. To give a user the ability to search the Office 365 audit log with the minimum level of privileges, you can create a custom role group in Exchange Online, add the View-Only Audit Logs or Audit Logs role, and then add the user as a member of the new role group. For more information, see Manage role groups in Exchange Online.
Important: If you assign a user the View-Only Audit Logs or Audit Logs role on the Permissions page in the Security & Compliance Center, they won't be able to search the Office 365 audit log. You have to assign the permissions in Exchange Online. This is because the underlying cmdlet used to search the audit log is an Exchange Online cmdlet.
-
You can search the Office 365 audit log for activities that were performed within the last 90 days.
-
It can take up to 30 minutes or up to 24 hours after an event occurs for the corresponding audit log entry to be displayed in the search results. The following table shows the time it takes for the different services in Office 365.
Office 365 service
30 minutes
24 hours
SharePoint Online and OneDrive for Business

Exchange Online

Azure Active Directory (user login events)

Azure Active Directory (admin events)

Sway

Power BI

Yammer

Security & Compliance Center

-
As previously stated, Azure Active Directory (Azure AD) is the directory service for Office 365. The unified audit log contains user, group, application, domain, and directory activities performed in the Office 365 admin center or in the in Azure management portal. For a complete list of Azure AD events, see Azure Active Directory Audit Report Events.
-
If you want to turn off audit log search in Office 365 for your organization, you can run the following command in remote PowerShell connected to your Exchange Online organization:
Set-AdminAuditLogConfig -UnifiedAuditLogIngestionEnabled $false
For more information, see Turn off audit log search in Office 365.
-
As previously stated, the underlying cmdlet used to search the audit log is an Exchange Online cmdlet, which is Search-UnifiedAuditLog. That means you can use this cmdlet to search the Office 365 audit log instead of using the Audit log search page in the Security & Compliance Center. You have to run this cmdlet in remote PowerShell connected to your Exchange Online organization. For more information, see Search-UnifiedAuditLog.
Step 1: Run an audit log search
-
Sign in to Office 365 using your work or school account.
-
In the left pane, click Search & investigation, and then click Audit log search.
The Audit log search page is displayed.
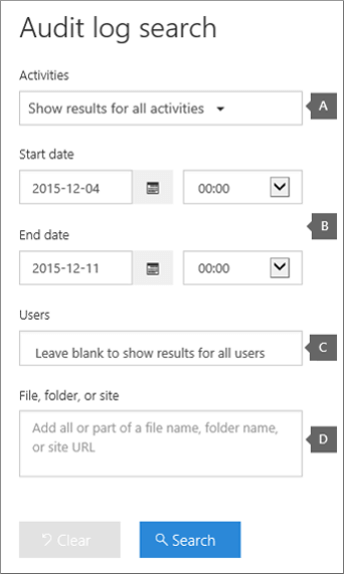
Note: As previously explained, you have to first turn on audit logging before you can run an audit log search. If the Start recording user and admin activity link is displayed, click it to turn on auditing. If you don't see this link, auditing has already been turned on for your organization.
-
Configure the following search criteria:
-
Activities Click the drop-down list to display the activities that you can search for. User and admin activities are organized in to groups of related activities. You can select specific activities or you can click the activity group name to select all activities in the group. You can also click a selected activity to clear the selection. After you run the search, only the audit log entries for the selected activities are displayed. Selecting Show results for all activities will display results for all activities performed by the selected user or group of users.
Over 100 user and admin activities are logged in the Office 365 audit log. See the Audited activities in Office 365 section in this topic for a description of each activity.
-
Start date and End date The last seven days are selected by default. Select a date and time range to display the events that occurred within that period. The date and time are presented in Coordinated Universal Time (UTC) format. The maximum date range that you can specify is 90 days. An error is displayed if the selected date range is greater than 90 days.
Tip: If you're using the maximum date range of 90 days, select the current time for the Start date. Otherwise, you'll receive an error saying that the start date is earlier than the end date. If you've turned on auditing within the last 90 days, the maximum date range can't start before the date that auditing was turned on.
-
Users Click in this box and then select one or more users to display search results for. The audit log entries for the selected activity performed by the users you select in this box are displayed in the list of results. Leave this box blank to return entries for all users (and service accounts) in your organization.
-
File, folder, or site Type some of all of a file or folder name to search for activity on the file of folder that contains the specified keyword. You can also specify a site URL or part of a URL to display entries for activity on any object in the specified URL path. Leave this box blank to return entries for all files, folders, and URLs in your organization.
-
-
Click Search to run the search using your search criteria.
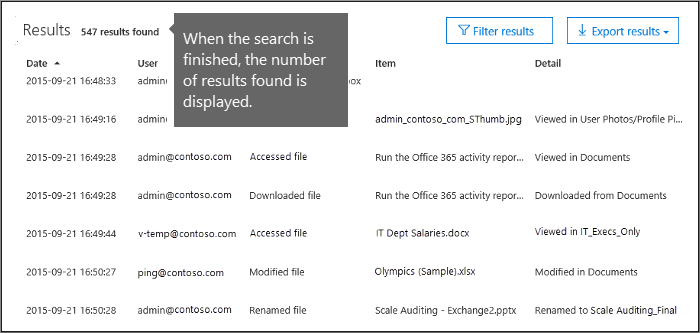
The search results are loaded, and after a few moments they are displayed under Results. When the search is finished, the number of results found is displayed. Note that a maximum of 1000 events will be displayed; if more than 1000 events meet the search criteria, the newest 1000 events are displayed.
Tips for searching the audit log
-
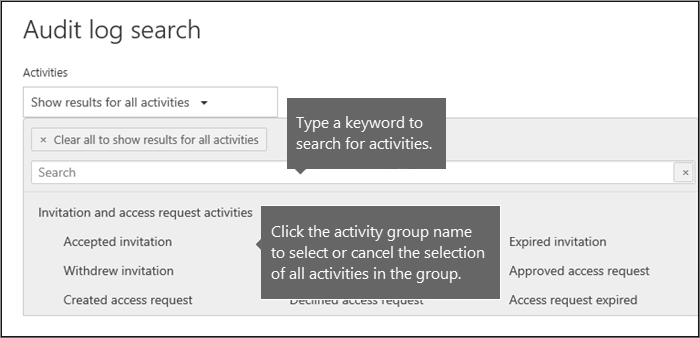
You can select specific activities to search for by clicking on the activity name. Or you can search for all activities in a group (such as File and folder activities) by clicking on the group name. If an activity is selected, you can click it to cancel the selection. You can also use the search box to display the activities that contain the keyword that you type.
-
You have to select Show results for all activities in the Activities list to display entries from the Exchange admin audit log. Events from this audit log display a cmdlet name (for example, Set-Mailbox) in the Activity column in the results. For more information, see the Exchange admin audit log section in this topic.
-
Click Clear to clear the current search criteria. The date range returns to the default of the last seven days. You can also click Clear all to show results for all activities to cancel all selected activities.
-
If 1000 results are found, you can probably assume there are more than 1000 events that met the search criteria. You can either refine the search criteria and rerun the search to return fewer results, or you can export all of the search results by selecting Export results > Download all results.
Step 2: View the search results
The results of an audit log search are displayed under Results on the Audit log search page. A maximum of 1000 (newest) events are displayed. The results contain the following information about each event returned by the search.
-
Date The date and time (in UTC format) when the event occurred.
-
IP address The IP address of the device that was used when the activity was logged. The IP address is displayed in either an IPv4 or IPv6 address format.
-
User The user (or service account) who performed the action that triggered the event.
-
Activity The activity performed by the user. This value corresponds to the activities that you selected in the Activities drop down list. For an event from the Exchange admin audit log, the value in this column is an Exchange cmdlet.
-
Item The object that was created or modified as a result of the corresponding activity. For example, the file that was viewed or modified or the user account that was updated. Not all activities have a value in this column.
-
Detail Additional detail about an activity. Again, not all activities will have a value.
Tip: Click a column header under Results to sort the results. You can sort the results from A to Z or Z to A. Click the Date header to sort the results from oldest to newest or newest to oldest.
View the details for a specific event
You can view more details about an event by clicking the event record in the list of search results. A Details page is displayed that contains the detailed properties from the event record. The properties that are displayed depend on the Office 365 service in which the event occurs. To display additional details, click More information.
Step 3: Filter the search results
In addition to sorting, you can also filter the results of an audit log search. This is a great feature that can help you quickly filter the results for a specific user or activity. You can initially create a wide search and then quickly filter the results to see specific events. Then you can narrow the search criteria and re-run the search to return a smaller, more concise set of results.
To filter the results:
-
Run an audit log search.
-
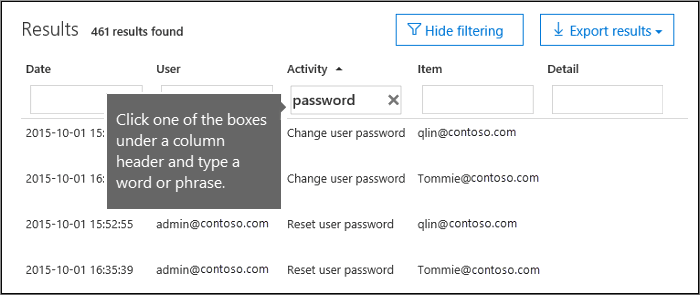
When the results are displayed, click Filter results.
Keyword boxes are displayed under each column header.
-
Click one of the boxes under a column header and type a word or phase, depending on the column you're filtering on. The results will dynamically readjust to display the events that match your filter.
-
To clear a filter, click the X in the filter box or just click Hide filtering.
Tip: To display events from the Exchange admin audit log, type a – (dash) in the Activity filter box. This will display cmdlet names, which are displayed in the Activity column for Exchange admin events. Then you can sort the cmdlet names in alphabetical order.
Step 4: Export the search results to a file
You can export the results of an audit log search to a comma separated value (CSV) file on your local computer. You can open this file in Microsoft Excel and use features such as search, sorting, filtering, and splitting a single column (that contains multi-value cells) into multiple columns.
-
Run an audit log search, and then revise the search criteria until you have the desired results.
-
Click Export results and select one of the following options:
-
Save loaded results Choose this option to export only the entries that are displayed under Results on the Audit log search page. The CSV file that is downloaded contains the same columns (and data) displayed on the page (Date, User, Activity, Item, and Details). An additional column (named More) is included in the CSV file that contains more information from the audit log entry. Because you're exporting the same results that are loaded (and viewable) on the Audit log search page, a maximum of 1000 entries are exported.
-
Download all results Choose this option to export all entries from the Office 365 audit log that meet the search criteria. For a large set of search results, choose this option to download all entries from the audit log in addition to the 1000 results that are displayed on the Audit log search page. This option will download the raw data from the audit log to a CSV file, and contains additional information from the audit log entry in a column named Detail. It may take longer to download the file if you choose this export option because the file may be much larger than the one that's downloaded if you choose the other option.
Important: You can download a maximum of 50,000 entries to a CSV file from a single audit log search. If 50,000 entries are downloaded to the CSV file, you can probably assume there are more than 50,000 events that met the search criteria. To export more than this limit, try using a date range to reduce the number of audit log entries. You might have to run multiple searches with smaller date ranges to export more than 50,000 entries.
-
-
After you select an export option, a message is displayed at the bottom of the window that prompts you to open the CSV file, save it to the Downloads folder, or save it to a specific folder.
More information about exporting audit log search results
-
The Download all results option downloads the raw data from the Office 365 audit log to a CSV file. This file contains different column names (Time, User, Action, Detail) than the file that's downloaded if you select the Save loaded results option. The values in the two different CSV files for the same activity may also be different. For example, the activity in the Action column in the CSV file and may have a different value than the "user-friendly" version that's displayed in the Activity column on the Audit log search page; for example, MailboxLogin vs. User signed in to mailbox.
-
If you download all results, the CSV file contains a column named Detail, which contains additional information about each event. As previously stated, this column contains a multi-value property for multiple properties from the audit log record. Each of the property:value pairs in this multi-value property are separated by a comma. You can use the Power Query in Excel to split this column into multiple columns so that each property will have its own column. This will let you sort and filter on one or more of these properties. To learn how to do this, see the "Split a column by delimiter" section in Split a column of text (Power Query).
After you split the Details column, you can filter on the Action column to display the detailed properties for a specific type of activity.
-
When you download all results from a search query that contains events from different Office 365 services, the Detail column in the CSV file contains different properties depending on which service the action was performed in. For example, entries from Exchange and Azure AD audit logs include a property named ResultStatus that indicates if the action was successful or not. This property isn't included for events in SharePoint. Similarly, SharePoint events have a property that identifies the site URL for file and folder related activities. To mitigate this behavior, consider using different searches to export the results for activities from a single service.
For a description of the properties that are listed in the Detail column in the CSV file when you download all results, and the service each one applies to, see Detailed properties in the Office 365 audit log.
Audited activities in Office 365
The following tables describe the activities that are audited in Office 365. You can search for these events by searching the audit log in the Security & Compliance Center. These tables are organized in the same sequence as they are in the Activities drop-down list on the Audit log search page. The tables include the friendly name that's displayed in the Activities drop-down list and the name of the event that appears in the Operation field in the Office 365 Management API schema and in the CSV file when you export the search results.
Sharing and access request activities
Site administration activities
User administration activities
Azure AD group administration activities
Application administration activities
Role administration activities
Directory administration activities
For information about Exchange admin activities, see the Exchange admin audit log section in this topic.
File and folder activities
The following table describes the file and folder activities in SharePoint Online and OneDrive for Business. The value in the Friendly name column is the activity name displayed in the Activities drop-down list on the Audit log search page and in the results. The value in the Operation column is the activity name from the Office 365 Management API schema.
| Friendly name | Operation | Description |
| Accessed file | FileAccessed | User or system account accesses a file. |
| Checked in file | FileCheckedIn | User checks in a document that they checked out from a document library. |
| Checked out file | FileCheckedOut | User checks out a document located in a document library. Users can check out and make changes to documents that have been shared with them. |
| Copied file | FileCopied | User copies a document from a site. The copied file can be saved to another folder on the site. |
| Deleted file | FileDeleted | User deletes a document from a site. |
| Discarded file checkout | FileCheckOutDiscarded | User discards (or undos) a checked out file. That means any changes they made to the file when it was checked out are discarded, and not saved to the version of the document in the document library. |
| Downloaded file | FileDownloaded | User downloads a document from a site. |
| Modified file | FileModified | User or system account modifies the content or the properties of a document located on a site. |
| Moved file | FileMoved | User moves a document from its current location on a site to a new location. |
| Renamed file | FileRenamed | User renames a document on a site. |
| Restored file | FileRestored | User restores a document from the recycle bin of a site. |
| Uploaded file | FileUploaded | User uploads a document to a folder on a site. |
Sharing and access request activities
The following table describes the user sharing and access request activities in SharePoint Online and OneDrive for Business. For sharing events, the Detail column under Results identifies the name of the user or group the item was shared with and whether that user or group is a member or guest in your organization. For more information, see Use sharing auditing in the Office 365 audit log.
Note: Users can be either members or guests based on the UserType property of the user object. A member is usually an employee, and a guest is usually a collaborator outside of your organization. When a user accepts a sharing invitation (and isn't already part of your organization), a guest account is created for them in your organization's directory. Once the guest user has an account in your directory, resources may be shared directly with them (without requiring an invitation).
| Friendly name | Operation | Description |
| Accepted access request | AccessRequestAccepted | An access request to a site, folder, or document was accepted and the requesting user has been granted access. |
| Accepted sharing invitation | SharingInvitationAccepted | User (member or guest) accepted a sharing invitation and was granted access to a resource. This event includes information about the user who was invited and the email address that was used to accept the invitation (they could be different). This activity is often accompanied by a second event that describes how the user was granted access to the resource, for example, adding the user to a group that has access to the resource. |
| Created a company shareable link | CompanyLinkCreated | User created a company-wide link to a resource. company-wide links can only be used by members in your organization. They can't be used by guests. |
| Created access request | AccessRequestCreated | User requests access to a site, folder, or document they don't have permissions to access. |
| Created an anonymous link | AnonymousLinkCreated | User created an anonymous link to a resource. Anyone with this link can access the resource without having to be authenticated. |
| Created sharing invitation | SharingInvitationCreated | User shared a resource in SharePoint Online or OneDrive for Business with a user who isn't in your organization's directory. |
| Denied access request | AccessRequestDenied | An access request to a site, folder, or document was denied. |
| Removed a company shareable link | CompanyLinkRemoved | User removed a company-wide link to a resource. The link can no longer be used to access the resource. |
| Removed an anonymous link | AnonymousLinkRemoved | User removed an anonymous link to a resource. The link can no longer be used to access the resource. |
| Shared file, folder, or site | SharingSet | User (member or guest) shared a file, folder, or site in SharePoint or OneDrive for Business with a user in your organization's directory. The value in the Detail column for this activity identifies the name of the user the resource was shared with and whether this user is a member or a guest. This activity is often accompanied by a second event that describes how the user was granted access to the resource; for example, adding the user to a group that has access to the resource. |
| Updated an anonymous link | AnonymousLinkUpdated | User updated an anonymous link to a resource. The updated field is included in the EventData property when you export the search results. |
| Used an anonymous link | AnonymousLinkUsed | An anonymous user accessed a resource by using an anonymous link. The user's identity might be unknown, but you can get other details such as the user's IP address. |
| Unshared file, folder, or site | SharingRevoked | User (member or guest) unshared a file, folder, or site that was previously shared with another user. |
| Used a company shareable link | CompanyLinkUsed | User accessed a resource by using a company-wide link. |
| Withdrew sharing invitation | SharingInvitationRevoked | User withdrew a sharing invitation to a resource. |
Synchronization activities
The following table lists file synchronization activities in SharePoint Online and OneDrive for Business.
| Friendly name | Operation | Description |
| Allowed computer to sync files | ManagedSyncClientAllowed | User successfully establishes a sync relationship with a site. The sync relationship is successful because the user's computer is a member of a domain that's been added to the list of domains (called the safe recipients list) that can access document libraries in your organization. For more information about this feature, see Use Windows PowerShell cmdlets to enable OneDrive sync for domains that are on the safe recipients list. |
| Blocked computer from syncing files | UnmanagedSyncClientBlocked | User tries to establish a sync relationship with a site from a computer that isn't a member of your organization's domain or is a member of a domain that hasn't been added to the list of domains (called the safe recipients list) that can access document libraries in your organization. The sync relationship is not allowed, and the user's computer is blocked from syncing, downloading, or uploading files on a document library. For information about this feature, see Use Windows PowerShell cmdlets to enable OneDrive sync for domains that are on the safe recipients list. |
| Downloaded files to computer | FileSyncDownloadedFull | User establishes a sync relationship and successfully downloads files for the first time to their computer from a document library. |
| Downloaded file changes to computer | FileSyncDownloadedPartial | User successfully downloads any changes to files from a document library. This activity indicates that any changes that were made to files in the document library were downloaded to the user's computer. Only changes were downloaded because the document library was previously downloaded by the user (as indicated by the Downloaded files to computer activity). |
| Uploaded files to document library | FileSyncUploadedFull | User establishes a sync relationship and successfully uploads files for the first time from their computer to a document library. |
| Uploaded file changes to document library | FileSyncUploadedPartial | User successfully uploads changes to files on a document library. This event indicates that any changes made to the local version of a file from a document library are successfully uploaded to the document library. Only changes are unloaded because those files were previously uploaded by the user (as indicated by the Uploaded files to document library activity). |
Site administration activities
The following table lists the events that result from site administration tasks in SharePoint Online.
| Friendly name | Operation | Description |
| Added exempt user agent | ExemptUserAgentSet | Global administrator adds a user agent to the list of exempt user agents in the SharePoint admin center. |
| Added site collection admin | SiteCollectionAdminAdded | Site collection administrator or owner adds a person as a site collection administrator for a site. Site collection administrators have full control permissions for the site collection and all subsites. |
| Added user or group to SharePoint group | AddedToGroup | User added a member or guest to a SharePoint group. This might have been an intentional action or the result of another activity, such as a sharing event. |
| Allowed user to create groups | AllowGroupCreationSet | Site administrator or owner adds a permission level to a site that allows a user assigned that permission to create a group for that site. |
| Changed exempt user agents | CustomizeExemptUsers | Global administrator customized the list of exempt user agents in the SharePoint admin center. You can specify which user agents to exempt from receiving an entire web page to index. This means when a user agent you've specified as exempt encounters an InfoPath form, the form will be returned as an XML file, instead of an entire web page. This makes indexing InfoPath forms faster. |
| Changed a sharing policy | SharingPolicyChanged | An administrator changed a SharePoint sharing policy by using the Office 365 admin portal, SharePoint admin portal, or SharePoint Online Management Shell. Any change to the settings in the sharing policy in your organization will be logged. The policy that was changed is identified in the ModifiedProperty field property when you export the search results. |
| Created group | GroupAdded | Site administrator or owner creates a group for a site, or performs a task that results in a group being created. For example, the first time a user creates a link to share a file, a system group is added to the user's OneDrive for Business site. This event can also be a result of a user creating a link with edit permissions to a shared file. |
| Created Sent To connection | SendToConnectionAdded | Global administrator creates a new Send To connection on the Records management page in the SharePoint admin center. A Send To connection specifies settings for a document repository or a records center. When you create a Send To connection, a Content Organizer can submit documents to the specified location. |
| Created site collection | SiteCollectionCreated | Global administrator creates a new site collection in your SharePoint Online organization. |
| Deleted group | GroupRemoved | User deletes a group from a site. |
| Deleted Sent To connection | SendToConnectionRemoved | Global administrator deletes a Send To connection on the Records management page in the SharePoint admin center. |
| Enabled document preview | PreviewModeEnabledSet | Site administrator enables document preview for a site. |
| Enabled legacy workflow | LegacyWorkflowEnabledSet | Site administrator or owner adds the SharePoint 2013 Workflow Task content type to the site. Global administrators can also enable work flows for the entire organization in the SharePoint admin center. |
| Enabled Office on Demand | OfficeOnDemandSet | Site administrator enables Office on Demand, which lets users access the latest version of Office desktop applications. Office on Demand is enabled in the SharePoint admin center and requires an Office 365 subscription that includes full, installed Office applications. |
| Enabled RSS feeds | NewsFeedEnabledSet | Site administrator or owner enables RSS feeds for a site. Global administrators can enable RSS feeds for the entire organization in the SharePoint admin center. |
| Enabled result source for People Searches | PeopleResultsScopeSet | Site administrator creates or changes the result source for People Searches for a site. |
| Modified site permissions | SitePermissionsModified | Site administrator or owner (or system account) changes the permission level that are assigned to a group on a site. This activity is also logged if all permissions are removed from a group. Note: This operation has been deprecated in SharePoint Online. To find related events, you can search for other permission-related activities such as Added site collection admin, Added user or group to SharePoint group, Allowed user to create groups, Created group, and Deleted group. |
| Removed user or group from SharePoint group | RemovedFromGroup | User removed a member or guest from a SharePoint group. This might have been an intentional action or the result of another activity, such as an unsharing event. |
| Renamed site | SiteRenamed | Site administrator or owner renames a site |
| Requested site admin permissions | SiteAdminChangeRequest | User requests to be added as a site collection administrator for a site collection. Site collection administrators have full control permissions for the site collection and all subsites. |
| Set host site | HostSiteSet | Global administrator changes the designated site to host personal or OneDrive for Business sites. |
| Updated group | GroupUpdated | Site administrator or owner changes the settings of a group for a site. This can include changing the group's name, who can view or edit the group membership, and how membership requests are handled. |
Exchange mailbox activities
The following table lists the activities that can be logged by mailbox audit logging. Mailbox activities performed by the mailbox owner, a delegated user, or an administrator are logged. By default, mailbox auditing in Office 365 isn't turned on. Mailbox audit logging must be turned on for each mailbox before mailbox activity will be logged. For more information, see Enable mailbox auditing in Office 365.
| Friendly name | Operation | Description |
| Copied messages to another folder | Copy | A message was copied to another folder. |
| Created or received messages | Create | An item is created in the Calendar, Contacts, Notes, or Tasks folder in the mailbox; for example, a new meeting request is created. Note that message or folder creation isn't audited. |
| Deleted messages from Deleted Items folder | SoftDelete | A message was permanently deleted or deleted from the Deleted Items folder. These items are moved to the Recoverable Items folder. Messages are also moved to the Recoverable Items folder when a user selects it and presses Shift+Delete. |
| Moved messages to another folder | Move | A message was moved to another folder. |
| Moved messages to Deleted Items folder | MoveToDeletedItems | A message was deleted and moved to the Deleted Items folder. |
| Purged messages from the mailbox | HardDelete | A message was purged from the Recoverable Items folder (permanently deleted from the mailbox). |
| Sent message using Send As permissions | SendAs | A message was sent using the SendAs permission. This means another user sent the message as though it came from the mailbox owner. |
| Sent message using Send On Behalf permissions | SendOnBehalf | A message was sent using the SendOnBehalf permission. This means another user sent the message on behalf of the mailbox owner. The message indicates to the recipient who the message was sent on behalf of and who actually sent the message. |
| Updated message | Update | A message or its properties was changed. |
| User signed in to mailbox | MailboxLogin | The user signed in to their mailbox. |
Sway activities
Note: We're still in the process of rolling out Sway audit logging to Office 365 organizations.
The following table lists user and admin activities in Sway. Sway is an Office 365 app that helps users gather, format, and share ideas, stories, and presentations on an interactive, web-based canvas. For more information, see Frequently asked questions about Sway – Admin Help.
| Friendly name | Operation | Description |
| Changed Sway share level | SwayChangeShareLevel | User changes the share level of a Sway. This event captures the user changing the scope of sharing associated with a Sway; for example, public versus inside the organization. |
| Created Sway | SwayCreate | User creates a Sway. |
| Deleted Sway | SwayDelete | User deletes a Sway. |
| Disabled Sway duplication | SwayDisableDuplication | User disables duplication of a Sway. |
| Duplicated Sway | SwayDuplicate | User duplicates a Sway. |
| Edited Sway | SwayEdit | User edits a Sway. |
| Enabled Sway duplication | EnableDuplication | User enables duplication of a Sway; the ability for a user to enable duplication of a Sway is enabled by default. |
| Revoked Sway sharing | SwayRevokeShare | User stops sharing a Sway by revoking access to it. Revoking access changes the links associated with a Sway. |
| Shared Sway | SwayShare | User intends to share a Sway. This event captures the user action of clicking a specific share destination within the Sway share menu. The event doesn't indicate whether the user completed the share action. |
| Turned off external sharing of Sway | SwayExternalSharingOff | Administrator disables external Sway sharing for the entire organization by using the Office 365 admin center. |
| Turned on external sharing of Sway | SwayExternalSharingOn | Administrator enables external Sway sharing for the entire organization by using the Office 365 admin center. |
| Turned off Sway service | SwayServiceOff | Administrator disables Sway for the entire organization by using the Office 365 admin center. |
| Turned on Sway service | SwayServiceOn | Administrator enables Sway for the entire organization by using the Office 365 admin center (Sway service is enabled by default). |
| Viewed Sway | SwayView | User views a Sway. |
User administration activities
The following table lists user administration activities that are logged when an admin adds or changes a user account by using the Office 365 admin center or the Azure management portal.
| Activity | Operation | Description |
| Added user | Add user | An Office 365 user account was created. |
| Changed user license | Change user license | The license assigned to a user what changed. To see what licenses were changes, see the corresponding Updated user activity. |
| Changed user password | Change user password | Administrator changed the password the password for a user. |
| Deleted user | Delete user | An Office 365 user account was deleted. |
| Reset user password | Reset user password | Administrator reset the password for a user. |
| Set property that forces user to change password | Set force change user password | Administrator set the property that forces a user to change their password the next time the user sign in to Office 365. |
| Set license properties | Set license properties | Administrator modifies the properties of a licensed assigned to a user. |
| Updated user | Update user | Administrator changes one or more properties of a user account. For a list of the user properties that can be updated, see the "Update user attributes" section in Azure Active Directory Audit Report Events. |
Azure AD group administration activities
The following table lists group administration activities that are logged when an admin or a user creates or changes an Office 365 group or when an admin creates a security group by using the Office 365 admin center or the Azure management portal. For more information about groups in Office 365, see View, create, and delete groups in the Office 365 admin center.
| Friendly name | Operation | Description |
| Added group | Add group | A group was created. |
| Added member to group | Add member to group | A member was added to a group. |
| Deleted group | Delete group | A group was deleted. |
| Removed member from group | Remove member from group | A member was removed from a group. |
| Updated group | Update group | A property of a group was changed. |
Application administration activities
The following table lists application admin activities that are logged when an admin adds or changes an application that's registered in Azure AD. Any application that relies on Azure AD for authentication must be registered in the directory.
| Friendly name | Operation | Description |
| Added delegation entry | Add delegation entry | A authentication permission was created/granted to an application in Azure AD. |
| Added service principal | Add service principal | An application was registered in Azure AD. An application is represented by a service principal in the directory. |
| Added credentials to a service principal | Add service principal credentials | Credentials were added to a service principal in Azure AD. A service principle represents an application in the directory. |
| Removed delegation entry | Remove delegation entry | A authentication permission was removed from an application in Azure AD. |
| Removed a service principal from the directory | Remove service principal | An application was deleted/unregistered from Azure AD. An application is represented by a service principal in the directory. |
| Removed credentials from a service principal | Remove service principal credentials | Credentials were removed from a service principal in Azure AD. A service principle represents an application in the directory. |
| Set delegation entry | Set delegation entry | An authentication permission was updated for an application in Azure AD. |
Role administration activities
The following table lists Azure AD role administration activities that are logged when an admin manages admin roles in the Office 365 admin center or in the Azure management portal.
| Friendly name | Operation | Description |
| Add member to Role | Add role member to role | Added a user to an admin role in Office 365. |
| Removed a user from a directory role | Remove role member from role | Removed a user to from an admin role in Office 365. |
| Set company contact information | Set company contact information | Updated the company-level contact preferences for your Office 365 organization. This includes email addresses for subscription-related email sent by Office 365, as well as technical notifications about Office 365 services. |
Directory administration activities
The following table lists Azure AD directory and domain related activities that are logged when an administrator manages their Office 365 organization in the Office 365 admin center or in the Azure management portal.
| Friendly name | Operation | Description |
| Added domain to company | Add domain to company | Added a domain to your Office 365 organization. |
| Added a partner to the directory | Add partner to company | Added a partner (delegated administrator) to your Office 365 organization. |
| Removed domain from company | Remove domain from company | Removed a domain from your Office 365 organization. |
| Removed a partner from the directory | Remove partner from company | Removed a partner (delegated administrator) from your Office 365 organization. |
| Set company information | Set company information | Updated the company information for your Office 365 organization. This includes email addresses for subscription-related email sent by Office 365, as well as technical notifications about Office 365 services. |
| Set domain authentication | Set domain authentication | Changed the domain authentication setting for your Office 365 organization. |
| Updated the federation settings for a domain | Set federation settings on domain | Changed the federation (external sharing) settings for your Office 365 organization. |
| Set password policy | Set password policy | Changed the length and character constraints for user passwords in your Office 365 organization. |
| Turned on Azure AD sync | Set DirSyncEnabled flag on company | Set the property that enables a directory for Azure AD Sync. |
| Updated domain | Update domain | Updated the settings of a domain in your Office 365 organization. |
| Verified domain | Verify domain | Verified that your organization is the owner of a domain. |
| Verified email verified domain | Verify email verified domain | Used email verification to verify that your organization is the owner of a domain. |
eDiscovery activities
Content Search and eDiscovery-related activities that are performed in Office 365 Security & Compliance Center or by running the corresponding Windows PowerShell cmdlets are logged in the Office 365 audit log. This includes the following activities:
-
Creating and managing eDiscovery cases
-
Creating, starting, and editing Content Searches
-
Performing Content Search actions, such as previewing, exporting, and deleting search results
-
Configuring permissions filtering for Content Search
-
Managing the eDiscovery Administrator role
For a list and detailed description of the eDiscovery activities that are logged, see Search for eDiscovery activities in the Office 365 audit log.
Power BI activities
The following table lists user and admin activities in Power BI that are logged in the Office 365 audit log.
| Friendly name | Operation | Description |
| Added Power BI group members | AddGroupMembers | A member is added to a Power BI group workspace. |
| Created Power BI dashboard | CreateDashboard | A new dashboard is created. |
| Created Power BI group | CreateGroup | A group is created. |
| Created organizational Power BI content pack | CreateOrgApp | An organizational content pack is created. |
| Deleted Power BI dashboard | DeleteDashboard | A dashboard is deleted. |
| Deleted Power BI datasets | DeleteDataset | A dataset is deleted. |
| Deleted Power BI report | DeleteReport | A report is deleted. |
| Downloaded Power BI report | DownloadReport | A user downloads a Power BI report from the service to their computer. |
| Edited Power BI dashboard | EditDashboard | A dashboard is renamed. |
| Exported Power BI report visual data | ExportReport | Data is exported from a report tile. |
| Exported Power BI tile data | ExportTile | Data is exported from a dashboard tile. |
| Printed Power BI dashboard | PrintDashboard | A dashboard is printed. |
| Printed Power BI report page | PrintReport | A report is printed. |
| Published Power BI report to web | PublishToWebReport | A report is published to the web. |
| Shared Power BI dashboard | ShareDashboard | A dashboard is shared. |
| Started Power BI trial | OptInForProTrial | A user starts a Power BI Pro trial subscription. |
| Updated organization's Power BI settings | UpdatedAdminFeatureSwitch | An admin changed an organizational setting in the Power BI admin portal. |
| Viewed Power BI dashboard | ViewDashboard | A dashboard is viewed. |
| Viewed Power BI report | ViewReport | A report is viewed. |
Yammer activities
The following table lists the user and admin activities in Yammer that are logged in the Office 365 audit log. To return Yammer-related activities from the Office 365 audit log, you have to select Show results for all activities in the Activities list. Use the date range boxes and the Users list to narrow the search results.
| Friendly name | Operation | Description |
| Accepted network usage policy | UsagePolicyAcceptance | User accepts the usage policy for the Yammer network. |
| Activated account | UserActivation | New user activates their account. |
| Added or removed network admin | NetworkAdminUpdated | Network or verified admin assigns or revokes network admin permissions to a user. |
| Added or removed verified admin | NetworkVerifiedAdminUpdated | Verified admin assigns or revokes verified admin permissions to a user. Only verified admins can perform this operation. |
| Added user to group | GroupJoined | User adds another user to a group. |
| Bulk-created new users | CsvUserImport | Verified admin uses a CSV file to create multiple user accounts. Only verified admins can perform this operation. |
| Changed data retention policy | SoftDeleteSettingsUpdated | Verified admin updates the setting for the network data retention policy to either Hard Delete or Soft Delete. Only verified admins can perform this operation. |
| Changed group privacy setting | GroupPrivacyToggled | Group admin changes the privacy setting of a group to Private Access or Public Access. |
| Changed network configuration | NetworkConfigurationUpdated | Network or verified admin changes the Yammer network's configuration. This includes setting the interval for exporting data and enabling chat. |
| Changed network profile settings | ProcessProfileFields | Network or verified admin changes the information that appears on member profiles for network users network. |
| Changed network usage policy | UsagePolicyUpdated | User updates the Yammer network's usage policy. |
| Changed private content mode | SupervisorAdminToggled | Verified admin turns Private Content Mode on or off. This mode lets an admin view posts in private groups and view private messages between individual users (or groups of users). Only verified admins only can perform this operation. |
| Changed security configuration | NetworkSecurityConfigurationUpdated | Verified admin updates the Yammer network's security configuration. This includes setting password expiration policies and restrictions on IP addresses. Only verified admins can perform this operation. |
| Created file | FileCreated | User uploads a file. |
| Created group | GroupCreation | User creates a new group. |
| Deleted file | FileDeleted | User deletes a file. |
| Deleted group | GroupDeletion | A group is deleted from Yammer. |
| Deleted message | MessageDeleted | User deletes a message. |
| Deleted network user | NetworkUserDeleted | Network or verified admin deletes a user from Yammer. Note: A network admin can't delete a verified admin. |
| Deleted user | UserDeletion | User account is deleted. |
| Downloaded file | FileDownloaded | User downloads a file. |
| Exported data | DataExport | Verified admin exports Yammer network data. Only verified admins can perform this operation. |
| Forced all users to log out | LogoutUsers | Verified admin forces all users to log out across all Yammer clients. Only verified admins can perform this operation. |
| Removed user from group | GroupMemberDeletion | User removes a member from a group. |
| Shared file | FileShared | User shares a file with another user. |
| Suspended network user | NetworkUserSuspended | Network or verified admin suspends (deactivates) a user from Yammer. |
| Suspended user | UserSuspension | User account is suspended (deactivated). |
| Updated file description | FileUpdateDescription | User changes the description of a file. |
| Updated file name | FileUpdateName | User changes the name of a file. |
| Viewed file | FileVisited | User views a file. |
Exchange admin audit log
Exchange administrator audit logging—which is enabled by default in Office 365—logs an event in the Office 365 audit log when an administrator (or a user who has been assigned administrative permissions) makes a change in your Exchange Online organization. Changes made by using the Exchange admin center or by running a cmdlet in Windows PowerShell are logged in the Exchange admin audit log. For more detailed information about admin audit logging in Exchange, see Administrator audit logging. Here are some tips for searching for activity in the Exchange admin audit log:
-
To return entries from the Exchange admin audit log, you have to select Show results for all activities in the Activities list. Use the date range boxes and the Users list to narrow the search results for cmdlets run by a specific Exchange administrator within a specific date range.
-
To display events from the Exchange admin audit log, filter the search results and type a – (dash) in the Activity filter box. This will display cmdlet names, which are displayed in the Activity column for Exchange admin events. Then you can sort the cmdlet names in alphabetical order.
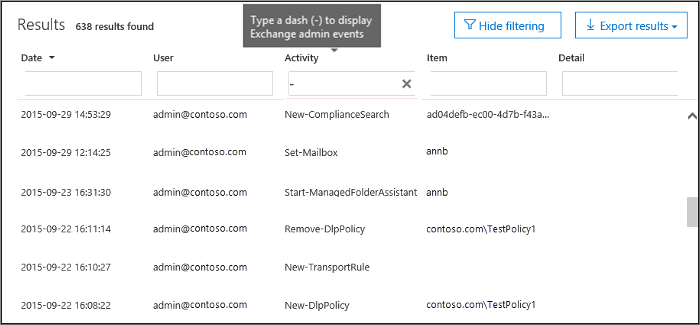
-
To get information about what cmdlet was run, which parameters and parameter values were used, and what objects were affected, you will have to export the search results and select the Download all results option.
This concept is a good way to enhance the knowledge.thanks for sharing..
ReplyDeleteOffice 365 Training
Office 365 Online Training
Nice post.
ReplyDeleteOffice 365 training
Open stack online training
Open stack training
SAP ABAP on Hana online training
SAP ABAP on Hana training
SAP ABAP online training
SAP ABAP training
SAP Basis online training
SAP Basis training
SAP Bods online training
SAP Bods training
SAP BW on Hana online training
SAP BW on Hana training
SAP CS online training
SAP CS training
SAP Fico online training
SAP Fico training
Nice post..
ReplyDeleteSAP Bods training
SAP BW on Hana training
SAP CS training
SAP Fico training
SAP Grc training
SAP Hana training
SAP mm training
SAP pm training
SAP PP training
SAP Qm training
sap bw on hana training
ReplyDeletesap sd training
osb training
oracle scm training
abinitio training