Protect yourself from phishing schemes and other forms of online fraud
This article describes what phishing is, how to determine phishing schemes, and best practices to avoid becoming a victim of online fraud.
For more information on staying safe online Visit the Microsoft Safety & Security Center.
In this article
If you receive a warning tip, why did you receive one and what should you do?

If you're receiving a warning tip about phishing there is a potential phishing scheme taking place. There are many ways that this can occur, which are outlined below; Microsoft uses algorithms, scoring systems, and machine learning to detect signals and warn you when there is a chance of phishing. You can learn more about how to report messages below.
Tip: If you get this warning on email messages from a sender you trust, and you have confirmed the warnings are a false alarm, add the sender to your Safe Senders list in Outlook. See Messages from a trusted sender are being flagged as phishing. How do I mark them as safe?
What is phishing, or online fraud?
Phishing (pronounced: fishing) is an online-fraud technique that is used by criminals to lure you into disclosing your personal information, which then enables the thief to:
-
Apply for and get credit in your name.
-
Empty your bank account and charge expenses to the limit of your credit cards.
-
Remove money from your accounts.
-
Use a copy of your debit card to withdraw your money from anywhere in the world.
Warning signs
It's likely that fraud is being tried when you are asked to:
-
Provide personal information to an unknown source.
-
Verify your account information with the threat of suspending your account.
-
Sell an item with a promise of payment that is much more than the item is worth.
-
Make direct monetary donations.
Tip: Use credit cards when making purchases online. If the card gets compromised, it's usually easier to dispute fraudulent charges on credit cards than other payment methods.
More information about phishing-scheme characteristics
Unfortunately, as phishing attacks become more sophisticated, it is very difficult for the average person to tell whether an email message or website is fraudulent. That is why phishing schemes are so prevalent and successful for criminals. For example, many fake email messages and websites link to real company logos of well-known brands. Therefore, they look legitimate. The following are several things that you can do to help protect yourself:
-
Requests for personal information in an email message Most legitimate businesses have a policy that they do not ask you for your personal information through email. Be very suspicious of a message that asks for personal information even if it might look legitimate.
-
Urgent wording Wording in phishing email messages is usually polite and accommodating in tone. It usually tries to get you to respond to the message or to click the link that is included in the message. To increase the number of responses, people try to create a sense of urgency so that you immediately respond without thinking. Usually, spoofed email messages are not personalized, although valid messages from your bank or e-commerce company generally are personalized.
-
Attachments Many phishing schemes ask you to open attachments, which can then infect your computer with a virus or spyware. If spyware is downloaded to your computer, it can record the keystrokes that you use to log on to your personal online accounts. Any attachment that you want to view should be saved first, and then scanned with an up-to-date antivirus program before you open it. To help protect your computer, Outlook automatically blocks certain attachment file types that can spread viruses. If Outlook detects a suspicious message, attachments of any file type in the message are blocked.
-
Fake or suspicious links People who create phishing messages are so sophisticated in their ability to create misleading links that it is impossible for the average person to tell whether a link is legitimate. It is always best to type the web address that you know is correct into your browser. Also, you can save the correct web address in your browser Favorites. Do not copy and paste web addresses from messages into your browser. Security alerts appear in the following situations:
-
You have a document open and you click a link to a website that has an address that has a potentially spoofed domain name.
-
You open a file from a website that has an address that has a potentially spoofed domain name. A Security Notice appears. Read the notice and make the selections that you want.
-
You can then choose whether to continue to visit the website. In this situation, we recommend that you click No on the Security Notice. This functionality helps to protect against homograph attacks.
-
If the Junk Email Filter does not consider a message to be spam but does consider it to be phishing, the message is left in the Inbox, but any links in the message are disabled and you cannot use the Reply and Reply All functionality.
-
If the Junk Email Filter considers the message to be both spam and phishing, the message is automatically sent to the Junk Email folder. Any message sent to the Junk Email folder is converted to plain text format and all links are disabled. In addition, the Reply and Reply All functionality is disabled. The InfoBar alerts you to this change in functionality.
-
If you click a link that was disabled in a phishing message, an Outlook Security dialog box appears. Make the selection that you want.
-
-
Link masks Though the link that you are urged to click might contain all or part of a real company's name, the link can be "masked." This means that the link you see does not take you to that address but somewhere different, usually a spoofed website. Resting the pointer on the link in an Outlook message can reveal another numeric Internet address. This should make you suspicious. Keep in mind that even the link in the box with the yellow background can be spoofed to look like a trustworthy web address.
-
Homographs A homograph is a word with the same spelling as another word but with a different meaning. In computers, a homograph attack is a web address that looks like a familiar web address but is actually altered. The purpose of spoofed web links that are used in phishing schemes is to deceive you into clicking the link.
Protect yourself from online fraud
-
Educate yourself Go to the Microsoft Safety & Security Center for information about how to protect your home computer with articles, information, and security programs.
-
Monitor your transactions Review your order confirmations and credit card and bank statements.
-
Use credit cards for transactions on the Internet In most locales, your personal liability is significantly limited.
More information about protecting yourself
Use the following best practices to avoid online fraud:
-
Never reply to email messages that request your personal information Be very suspicious of any email message from a business or person who asks for your personal information, or one that sends you personal information and asks you to update or confirm it. Instead, use the phone number from one of your statements to call the business. Do not call a number listed in the email message. Similarly, never volunteer any personal information to someone who places an unsolicited call to you.
-
Don't click links in suspicious emails Don't click a link in a suspicious message. The link might not be trustworthy. Instead, visit websites by typing their URL into your browser or by using your Favorites link. Do not copy and paste links from messages into your browser.
-
Don't send personal information in regular email messages Regular email messages are not encrypted and are like sending a post card. If you must use email messages for personal transactions, use Outlook to digitally sign and encrypt messages by using S/MIME security. MSN, Microsoft Hotmail, Microsoft Outlook Express, Microsoft Office Outlook web Access, Lotus Notes, Netscape, and Eudora all support S/MIME security.
-
Do business only with companies that you know and trust Use well-known, established companies with a reputation for quality service. A business website should always have a privacy statement that specifically states that the business won't pass your name and information to other people.
-
Make sure the website uses encryption The web address should be preceded by https:// instead of the usual http:// in the browser's Address bar. Also, double-click the lock icon on your browser's status bar to display the digital certificates for the site. The name that follows Issued to in the certificate should match the site that you think you are on. If you suspect that a website is not what it should be, leave the site immediately and report it. Don't follow any of the instructions that it presents.
-
Monitor your transactions Review your order confirmations and credit-card and bank statements when you receive them to make sure that you are being charged only for transactions you made. Immediately report any irregularities in your accounts by dialing the number shown on your account statement. Using just one credit card for online purchases makes it easier to track your transactions.
-
Use credit cards for transactions on the Internet In most locales, your personal liability in case someone compromises your credit card is significantly limited. By contrast, if you use direct debit from your bank account or a debit card, your personal liability frequently is the full balance of your bank account. In addition, a credit card with a small credit limit is preferable for use on the Internet because it limits the amount of money that a thief can steal in case the card is compromised. Some major credit card issuers may offer customers the option of shopping online with virtual, single-use credit card numbers that expire within one or two months. If the service is available in your country or region, your bank can provide you with details about perishable virtual credit-card numbers.
How do I report online fraud and identity theft?
If you think that you received a fraudulent email message you can report the problem and attach the suspicious message. Reporting suspicious messages to authorities helps combat identity theft.
Forward an email as an attachment in Outlook 2016, Outlook 2013, or Outlook 2010
-
Select, but don't open the message that you want to report.
-
On the Home tab, in the Respond group, click More.
-
Select Forward as Attachment.
-
In the To line, type the email address of the company or organization to whom you are reporting the suspicious message.
-
Click Send.
Forward an email as an attachment in Windows Mail
-
Select, but don't open the message that you want to report.
-
On the Message menu, click Forward as Attachment.
-
In the To line, type the email address of the company or organization to whom you are reporting the suspicious message.
-
Click Send.
More resources
-
For Microsoft-related issues, you can send email to:
-
abuse@msn.com
-
abuse@microsoft.com
-
Messages from a trusted sender are being flagged as phishing. How do I mark them as safe?
If you trust the sender you can add them to Outlook's Safe Senders list.
-
Click Junk > Junk Email Options.
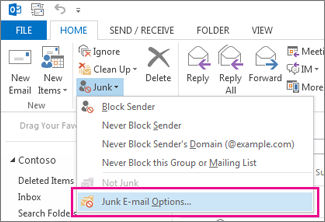
-
On the Junk Email Options dialog box choose Safe Senders.
-
Click Add and enter the email address or domain name.
Repeat for any additional addresses you want to add.
-
Click OK back out.
Messages from addresses on the Safe Senders list shouldn't be flagged as potential phishing messages.
No comments:
Post a Comment